~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~~~~~
⚙️ Discover my series on Automation of cybersecurity measures. THE Coded.
🔒 Related Stories: Application security | security code | AWS Security
💻 Free content on Cybersecurity Jobs | ✉️ Register for Broadcast list
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~~~~~
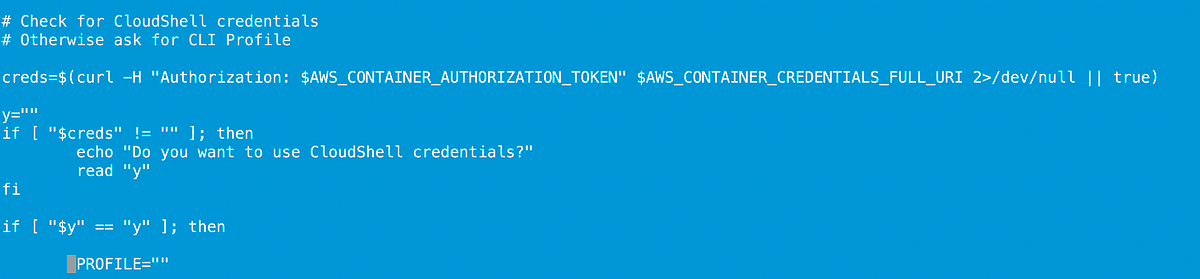
In the last article, I explained how to reduce the blast radius and improve security when using personal access tokens with a GitHub organization.
Now I’m trying to use the tokens with my new organization to complete the code I was working on when I stopped before.
It’s always interesting to step away from your code and come back and try to figure out what you were doing. My goal is to continually improve and simplify the execution of my code while keeping it secure.
One of the good things I did was create a repository with a fairly self-explanatory name:
test-2sl-job-exec
If you want to run a job, you use code from this repository.
Maybe I could improve further by making things more obvious, but I have a run_local.sh script in this repository to run a task on a local host rather than in a container. I ran this script to see what failed and where I stopped.
The first thing I noticed was that when I ran the script, it listed all the tasks I configured in previous tests. I no longer remembered the position I was supposed to occupy. I had four previously configured tasks in various undo states. Imagine if there were hundreds of jobs! I’ll have to think about it, but a comment on the setting might help, since this task list is derived from the SSM setting names.
I choose the most likely candidate after reviewing the configuration and running the job.
From there I remember, oh yes, it’s building a container with everything…