~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~
⚙️ Discover my series on Automation of cybersecurity measures | Coded.
🔒 Related Stories: Apple Mac Security | Internet Security | Data breaches
💻 Free content on Cybersecurity Jobs | ✉️ Register for Broadcast list
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~
I started looking at strange happenings on one of my laptops here:
In this article, I’ll delve deeper into a special type of file that sends data between processes in Linux.
Unix, Linux, and Mac provide a way to transfer program data from one command to another. For example, I used the cat command in a previous article to concatenate all files in a log directory:
cat *
Then I used a pipe and sent the result of this command to grep.
cat * | grep "something I'm looking for in those logs"
You can also send the result of a command to a file:
cat * | grep "something I'm looking for in those logs" > results.txt
If you use the command above, it will overwrite results.txt with the commands data every time you run it. If you want to add the data every time you run it, you can use this command:
cat * | grep "something I'm looking for in those logs" >> results.txt
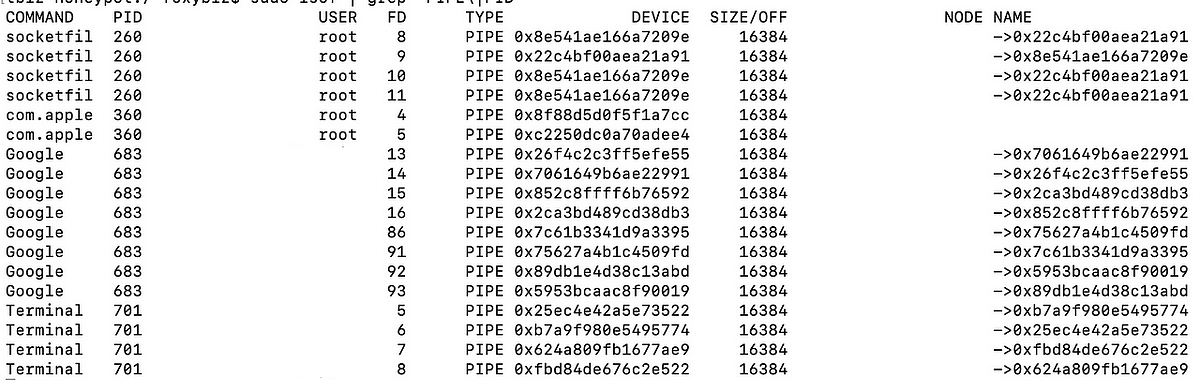
A named pipe in Linux or Mac is a special file used to transfer data between processes. Sometimes these types of files or commands are used by malware or harmful commands on your system.
I’m not going to explain everything about pipes in this article but I will show you how to look at PIPE-like processes in the results of the lsof command that I demonstrated in previous articles.