~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~~~~~
⚙️ Discover my series on Automation of cybersecurity measures. THE Coded.
🔒 Related Stories: GitHub Security | Application security | Data breaches
💻 Free content on Cybersecurity Jobs | ✉️ Register for Broadcast list
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~~~~~
A recent Mercedes-Benz compromise showed that attackers could have accessed their entire source code.
Bleeping Computer contains the following information:
“The GitHub token provided “unlimited” and “unmonitored” access to the entire source code hosted on the internal GitHub Enterprise server,” it read. RedHunt Labs Report.
Here’s how you can avoid a similar scenario in your organization.
Fine-grained tokens and token restrictions
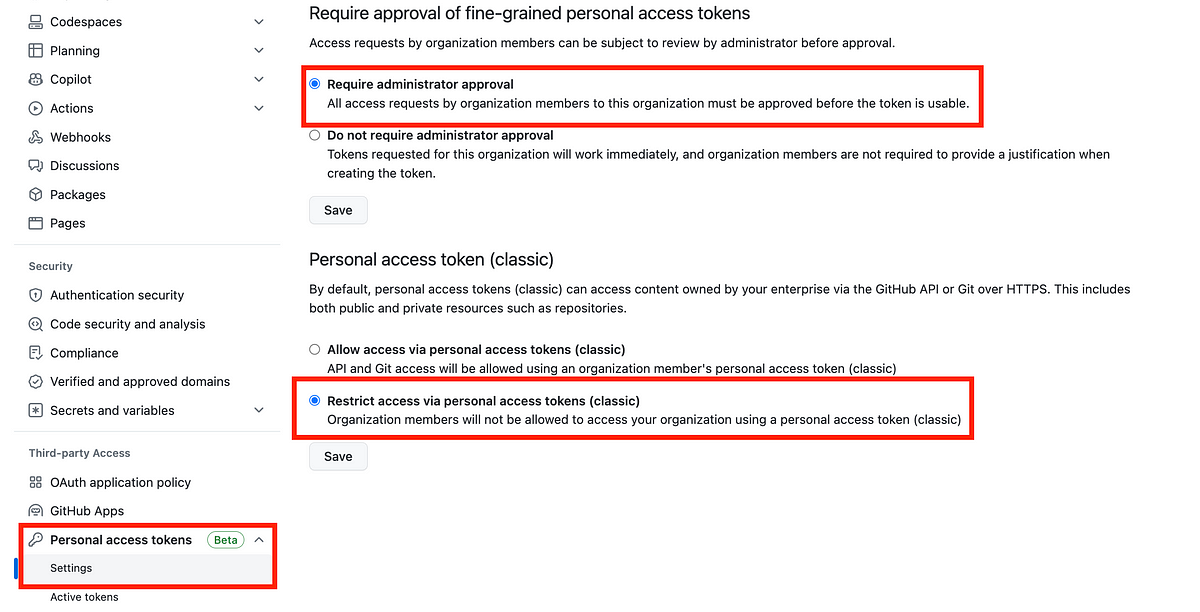
First, create fine-grained personal access tokens. This means that when you grant permission to an access token, you are not giving it access to everything. You limit this access to certain accounts. Refuse classic tokens.
You can prevent people from using classic tokens in your organization settings. Scroll down to Personal Access Tokens.
Require approval before a new token can be used and ensure it has limited permissions, not “everything” access.
Prohibit the creation of classic tokens that have access to “everything”.