ACM.431 A naming convention to provide a list of tasks that a user can perform to deploy resources to an AWS account
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~~~~~
⚙️ Part of my series on Automation of cybersecurity measures. THE Coded.
🔒 Related Stories: AWS Security | Application security | Abstraction
💻 Free content on Cybersecurity Jobs | ✉️ Register for Broadcast list
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~ ~~~~~~
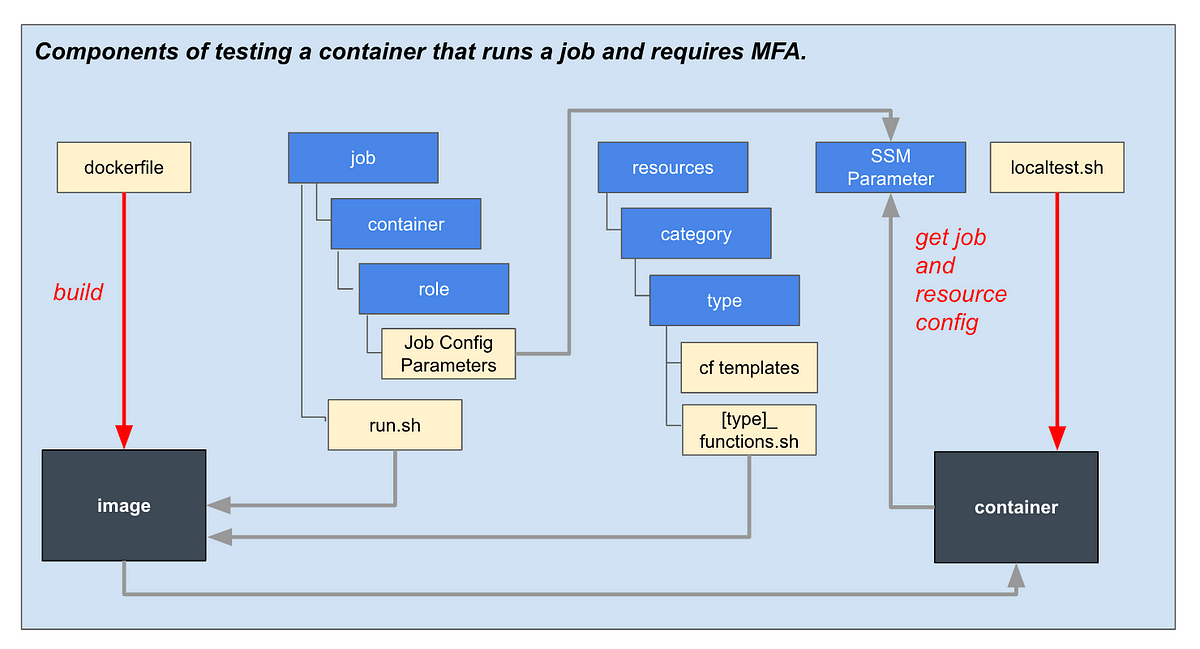
In the last article I was thinking about settings management architecture.
I want to implement a way to use AWS SSM settings for deployments and will test some options.
The idea is that I want to separate the data plane (the description of what to deploy) from the control plane (the application that deploys the resource).
You already get this to some extent with CloudFormation. You specify what to deploy and your CloudFormation template deploys it. You have no control over the deployment engine.
However, there is significant complexity and possible configuration errors in CloudFormation templates. I always tell customers to avoid security configuration mistakes, to provide approved templates that people in an organization can use to quickly deploy new things in a compliant manner, without an arduous approval process.
If they want to create something different, they just need to go through proper review and testing, while they can quickly spin up already configured assets in an approved manner.
So that’s what I’m doing here. I have a container that deploys some basic resources in an approved manner based on a configuration provided by a user.
The person providing the configuration may not know all the security details and this is handled on their behalf. But if they wanted to deploy something different, they could come up with a new configuration to add to the deployment engine.