Scams
The race to AI is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see for themselves what all the hype is about. The heyday of cybercriminals!
August 21, 2023
•
,
4 minutes. read

My first “huh?” The timing was that the shortened URL did not include any Google references but rather a link to rebrand.ly – a service with no obvious connection to Google and with offices in Dublin, Ireland. It seemed strange that an Internet giant would use the services of another provider and my suspicions were aroused. I then reread the ad text and although I’m not a native English speaker, I found it hard to believe that no one seemed to have reread this rather confusing content.
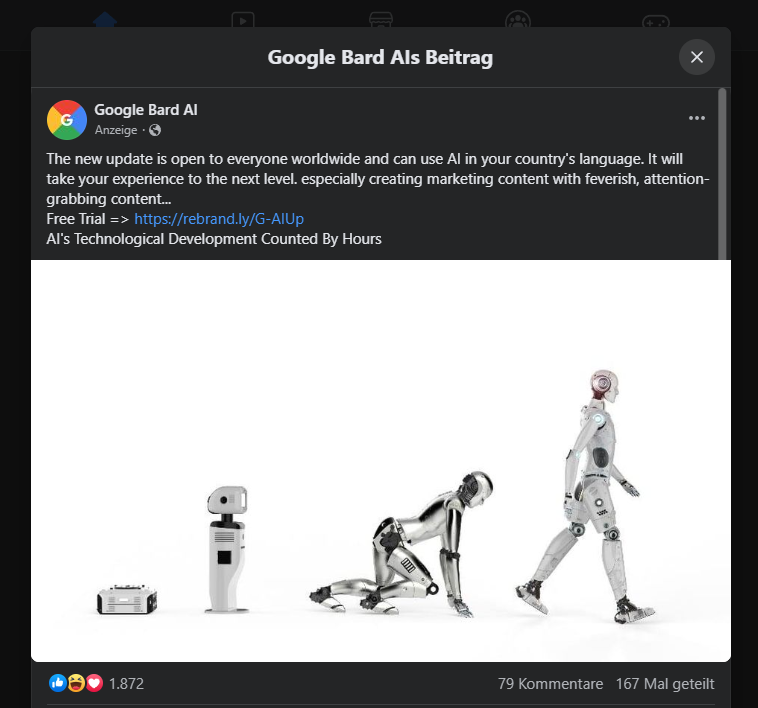
Did you say “Bots”?
I then checked the comments section under the ad for clues about possible fraud, but to my (little) surprise, they all seemed to like “the app.” Referring only to “app” seemed rather general, while others praised “AI” without ever mentioning Google. Some gave “a 5 star rating” (sic) – in a comments section?! Somehow, miraculously, it seemed like everyone in the comments had downloaded and tested the app at the same time, only to then write their comments at exactly the same time – which in my case was “6 hours ago” – only adding to my suspicions.
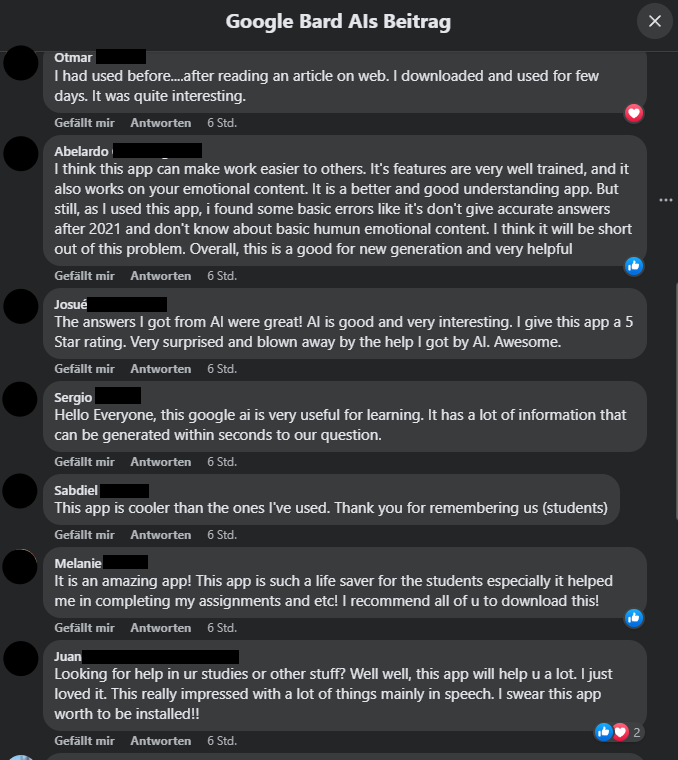
Follow the trail
I chose to turn on my protected environment to investigate a little further. First, I checked rebrandly’s link on VirusTotalwhich was flagged as malicious by 3 out of 90 vendors. This is an early indicator, but it is by no means proof, as it could also be a false positive.
So I went ahead and opened the link in an anonymous browser window – which turned out to be a perfect idea since the link led to a real Google site – hxxps://sites.google.com/view/12345328?fbclid=IwAR2V87sG77nklWVC1tLS-R-fjrL_nNNDhjtDorxKHkN56g8oNVV09Edjgwo
If I had accessed the site while logged in to my browser, especially with my Google account in Chrome, the criminals would have potentially obtained a lot more information about me than I would have liked!
Although the site is hosted on Google’s cloud infrastructure, the content is of course neither linked to nor provided by Google itself. This also gives a few more clues that something fishy is about to happen here. First, let’s look at the page title on the browser tab: “Trang chủ” (Vietnamese for “home page”). Furthermore, it seems obvious, once again, that the text on the site was not created by a native or proficient English speaker. This suggests that the attackers behind this campaign are based in Vietnam, but of course, this is by no means sufficient proof.
The “Download” button then leads to hxxps://drive.google.com/u/0/uc?id=1sn-Lzt-2vJ_i-6I9lkbGgr_-IN2TVcA-&export=download – a personal Google Drive space, trying to create the illusion that the campaign was an official offer from Google, when it was simply a cheap means of distribution for the attackers.
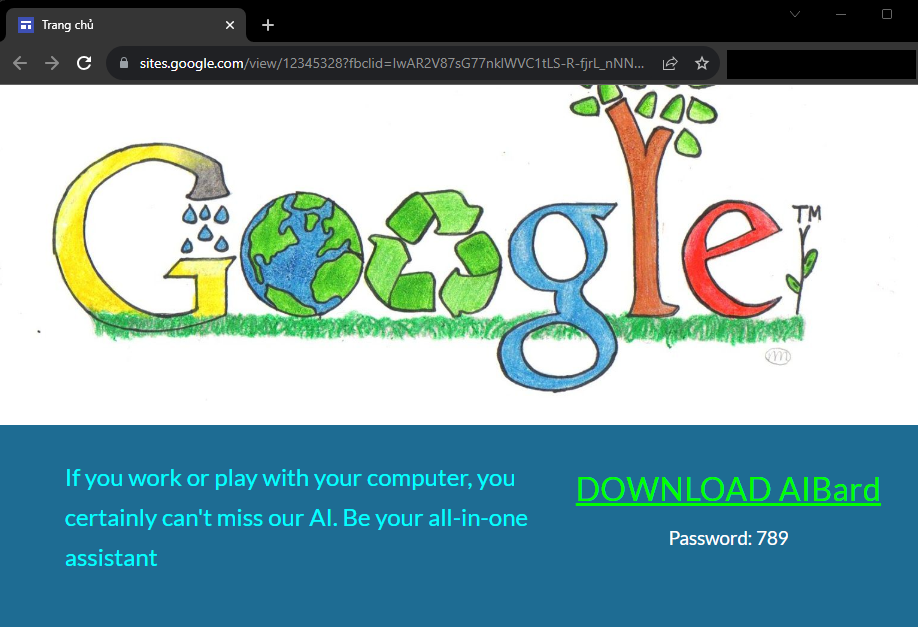
There is no intelligence, even artificial
The downloaded file is a RAR archive – GoogleAIUpdata.rar. Scanning it or uploading it to VirusTotal doesn’t lead to anything useful because it is “password protected.” One might wonder why if it was a real download from Google, you say? Well, this password “protection” only acts as an easy way for attackers to bypass malware scanners – nothing else. If you open the archive (without unpacking it!) with the password “789” as indicated on the download page, you will see that the archive contains an installer in the MSI (Microsoft software installer)format – Configuring Google Bard AI.msi. Fortunately, unarchiving tools like 7-zip offer the ability to create hashes of SHA-256 (and other) files, which can then be searched on VirusTotal, again, without the need to unzip a potentially harmful file.
Searching for the file provides the latest evidence that it is a malicious campaign. 26/59 sellers report file as maliciousESET giving a little more information in the detection name. JS/ExtenBro.Agent.EK is a JavaScript agent that will attempt to modify your browser settings, preventing access to certain security provider sites to get rid of them after infection, but it mainly serves as Adwaredisplaying annoying and unwanted advertisements on virtually every website you try to access and promising attackers money for each advertisement displayed on a victim’s machine.
Conclusion
At the time of writing, the campaign was still visible in different variations, but I reported it and I certainly won’t be the only one to do so. Unfortunately, it appears to be a larger campaign, as I have now come across other examples such as “meta-AI” or other fake “Google AI” ads. After all, this campaign can be seen as a desperate attempt to make a quick buck from the current and ongoing AI hype, pushing out ever more annoying adware to make even more money. This is by no means a sophisticated campaign. But the sad reality is that people fall for such scams in the hope of getting their hands on the latest technology. Another sad truth is that we cannot rely on tech giants like Facebook and Google to provide 100% clean and safe environments.
I hope this blog post helps you a little to spot the odds and clues and investigate a potential scam or malware attack without the need for expensive tools, right from home.

