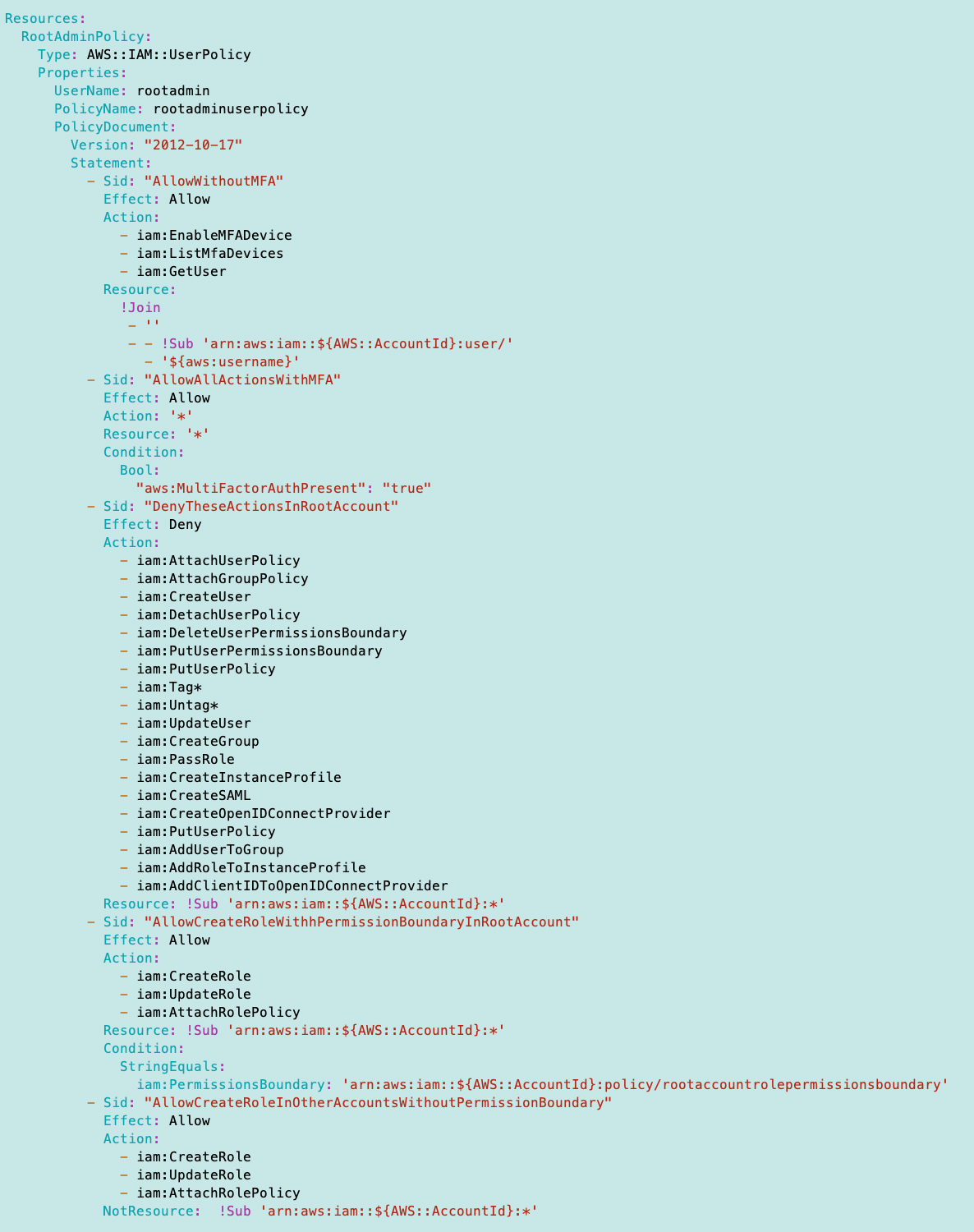
ACM.375 scripts to deploy the rootadmin (orgroot) user with restrictions covered in the latest articles
Part of my series on Automation of cybersecurity measures. AWS Organizations. I AM. Deploy a static website. THE Coded.
Free content on Cybersecurity Jobs | Register at Broadcast list
In the last article I looked at the users, groups, roles and policies we want to create as a whole in our initial architecture.
I had started this path earlier but never finished it. Now I want to do it, with a new deployment mechanism and a new directory structure.
In this article I will basically deploy the OrgRoot user again but named root administrator to align with our new naming convention – reasons provided in previous posts.
AWS Console Shell
Since we don’t want to grant developer credentials to the root user, we will use the AWS shell to create this initial user and policy.
After that I’ll probably end up locking this shell so it can’t be accessed. A user can achieve the same functionality on an AWS EC2 instance.
I’ll use the same approach as before, copying and pasting existing scripts into the shell and running them.
New directory structure
The first thing I do is copy the user model into my new directory structure and naming convention as I create each resource, although in this case I’ll just copy the files into my directory root in CloudShell to create the resources. for simplicity.