ESET Research
How ESET Research discovered a kill switch that was used to take down one of the most prolific botnets on the market
November 1, 2023
•
,
3 minutes. read

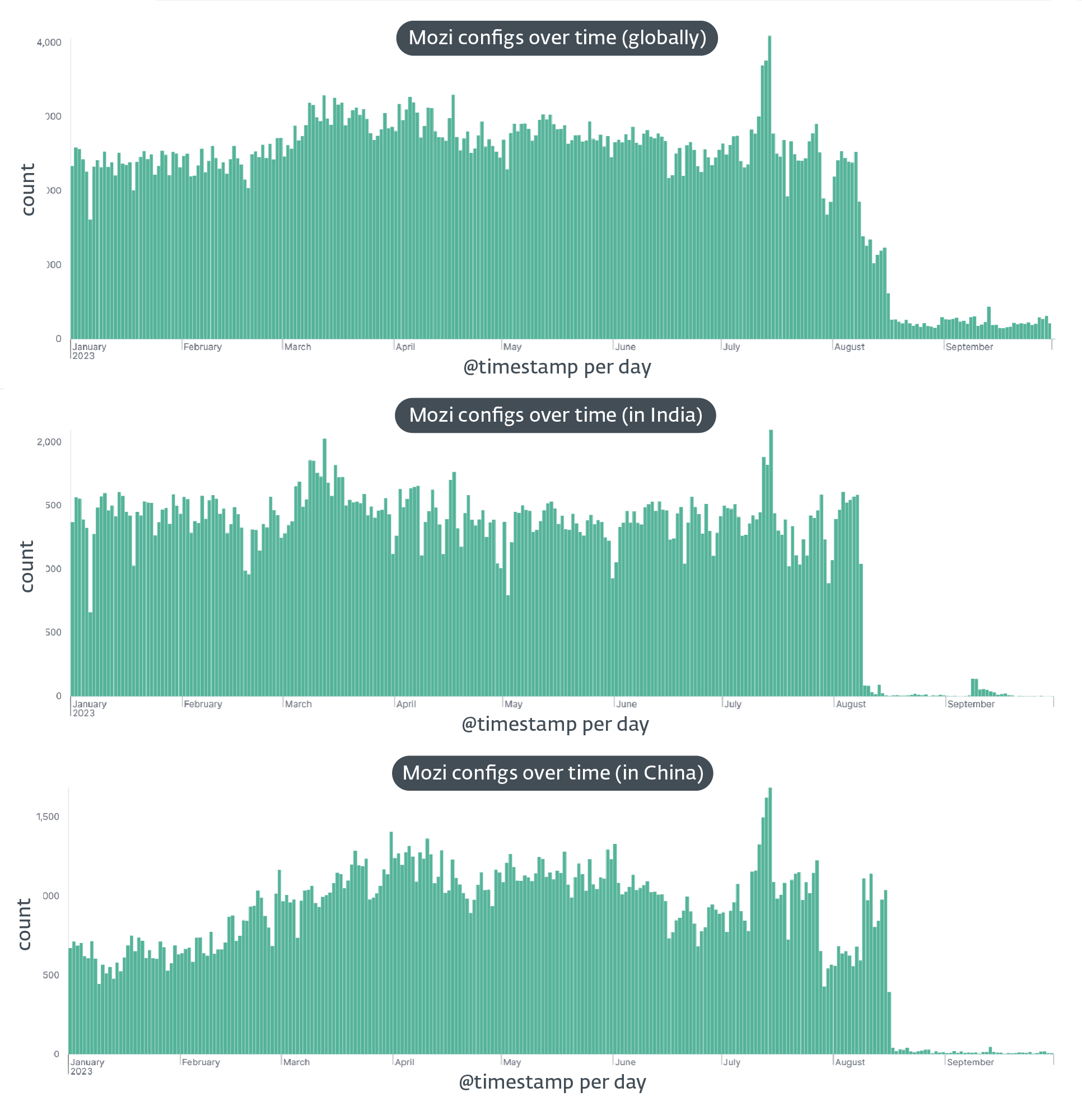
In August 2023, the notorious Mozi botnet, infamous for exploiting vulnerabilities in hundreds of thousands of IoT devices each year, experienced a sudden and unanticipated drop in activity. First observed in India on August 8th2023 and a week later in China on August 16thThis mysterious disappearance deprived Mozi robots of most of their functionalities.
Our investigation into this event led us to the discovery of a kill switch on September 27th, 2023. We spotted the control payload (configuration file) in a User Datagram Protocol (UDP) message that lacked the typical encapsulation of BitTorrent’s Distributed Sloppy Hash Table (BT-DHT) protocol. The person behind the takedown sent the control payload eight times, each time asking the bot to download and install an update on its own over HTTP.
The kill switch demonstrated several features, including:
- kill the parent process, i.e. the original Mozi malware,
- disable some system services such as sshd and dropbear,
- replace the original Mozi file with itself,
- execute some router/device configuration commands,
- disable access to various ports (iptables -j DROP), And
- establishing the same anchor as the original Mozi file being replaced
We identified two versions of the control payload, the latter functioning as a wrapper containing the former with minor modifications, such as adding a function to ping a remote server, likely intended for statistical purposes.
Despite the drastic reduction in functionality, Mozi bots maintained their persistence, indicating a deliberate and calculated withdrawal. Our analysis of the kill switch shows a strong link between the botnet’s original source code and recently used binaries, as well as the use of the correct private keys to sign the control payload (see Figure 2).
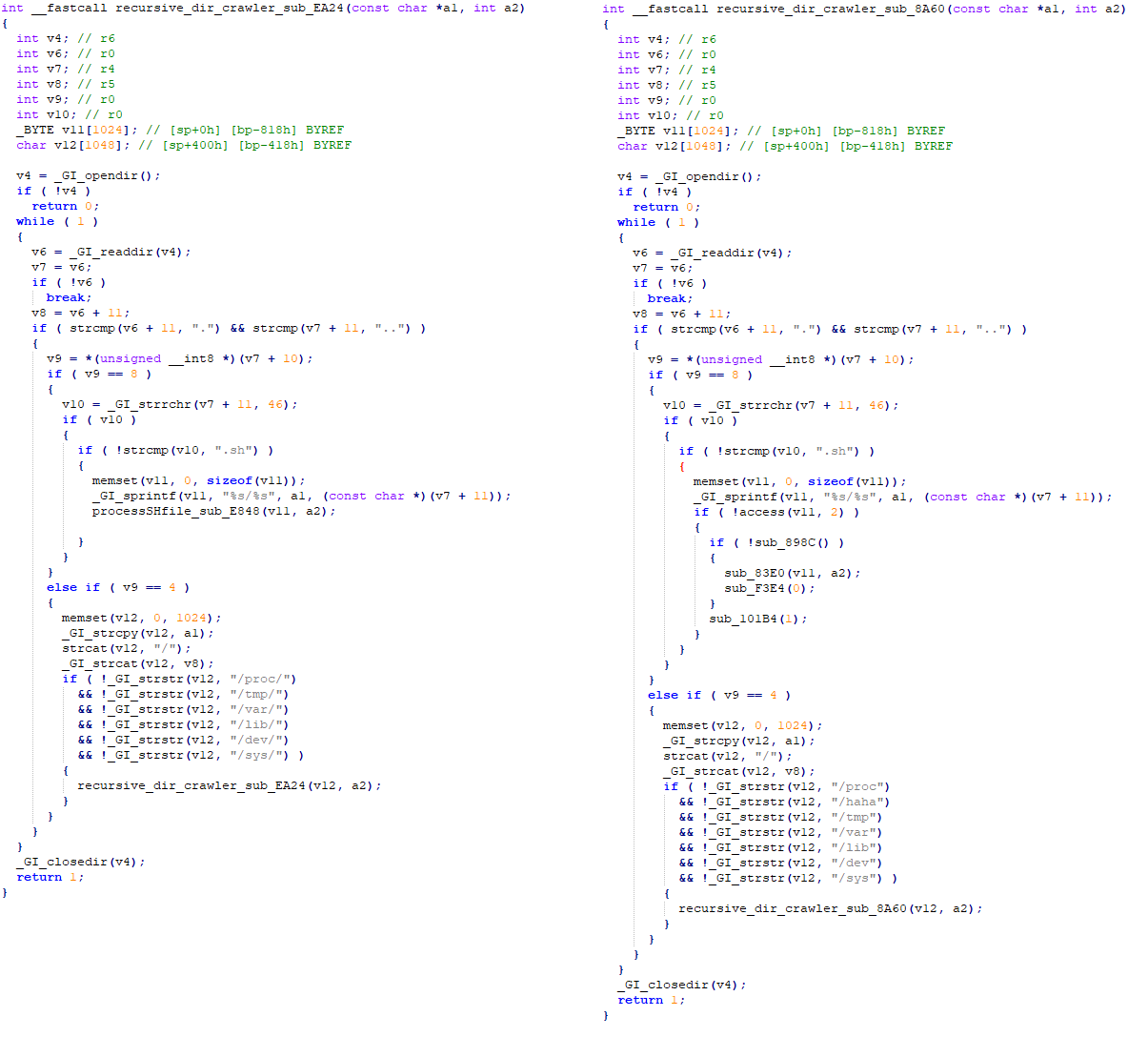
This brings us to the hypothesis suggesting two potential authors of this dismantling: the creators of the Mozi botnet, or Chinese law enforcement forcing the cooperation of the creators. The sequential targeting of bots in India and then China suggests that the takedown was carried out deliberately, with one country targeted first and the other a week later.
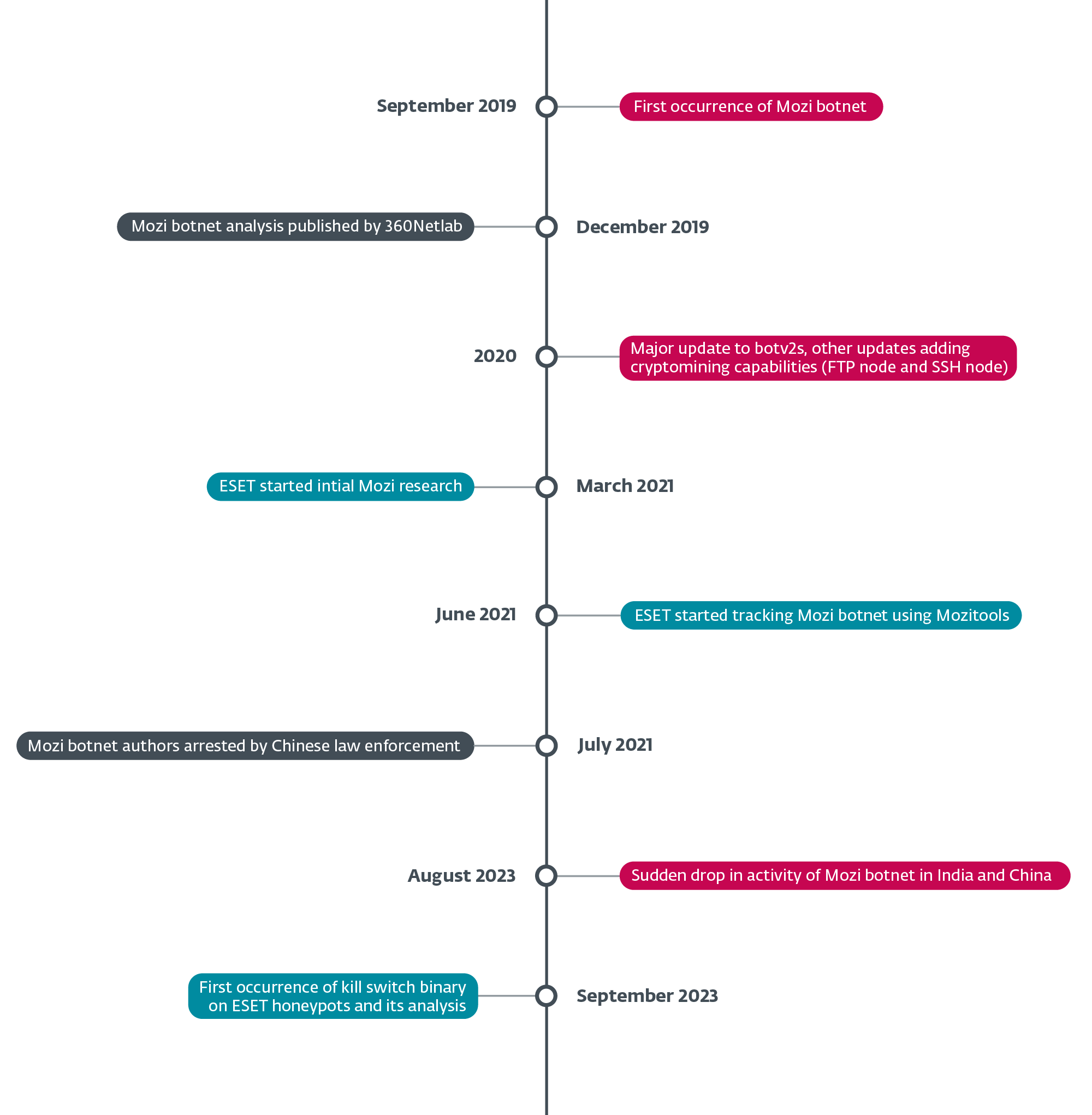
The demise of one of the most prolific IoT botnets is a fascinating case of cybercrime, providing us with fascinating technical insights into how these wild botnets are created, exploited and dismantled. We are continuing our investigation into this matter and will publish a detailed analysis in the coming months. But for now, the question remains: who killed Mozi?
For any inquiries about our research published on WeLiveSecurity, please contact us at menaceintel@eset.com.
ESET Research offers intelligence reports and private APT data feeds. For any inquiries about this service, visit ESET Threat Intelligence page.
IoC
Files
|
SHA-1 |
File name |
Detection |
Description |
|
758BA1AB22DD37F0F9D6FD09419BFEF44F810345 |
mozi.m |
Linux/Mozi.A |
Original Mozi bot. |
|
9DEF707F156DD4B0147FF3F5D1065AA7D9F058AA |
ud.7 |
Linux/Mozi.C |
Mozi robot stop button. |
Network
|
IP |
Domain |
Hosting Provider |
Seen the first time |
Details |
|
157.119.75(.)16 |
N / A |
AS135373 EFLYPRO-AS-AP EFLY NETWORK LIMITED |
2023-09-20 |
Kill Switch Hosting Server |
MITER ATT&CK Techniques
This table was constructed using version 13 of the MITER ATT&CK framework.
|
Tactical |
IDENTIFIER |
Name |
Description |
|
Resource development |
Acquire infrastructure: virtual private server |
Mozi’s kill switch operators rented a server from eflycloud.com to host the update files. Mozi’s kill switch operators have leased several servers that send payloads over BT-DHT networks. |
|
|
Initial access |
Operate a public application |
The Mozi kill switch operators sent an update command to Mozi customers on a BT-DHT network. |
|
|
Persistence |
Boot or login initialization scripts: RC scripts |
The kill switch creates several scripts, such as /etc/rc.d/rc.localto establish persistence. |
|
|
Exfiltration |
Exfiltration via an alternative protocol: Exfiltration via an unencrypted non-C2 protocol |
The kill switch sends an ICMP ping to the operator, perhaps for monitoring purposes. |
|
|
Impact |
Service shutdown |
The kill switch stops the SSH service and blocks access to it with iptables. |


