Part of my series on Automation of cybersecurity measures. AWS Organizations. I AM. Deploy a static website. THE Coded.
Free content on Cybersecurity Jobs | Register at Broadcast list
In my last article, I explained how to end an AWS CLI session.
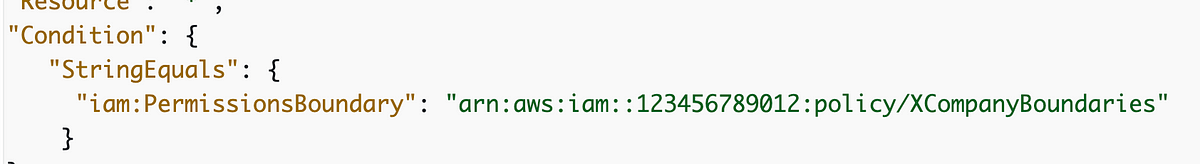
In this article I want to try to prevent privilege escalation using an AWS IAM permission boundary. I wrote about IAM permission limits in this article.
Keep this complication in mind if you use a permission limit. If you apply a permission limit to an existing principal who accesses resources, they may be excluded from items they need access to. I’ve seen issues like this make S3 buckets inaccessible when the administrator was the only one allowed to manage the bucket. I don’t know why this problem exists and why AWS can’t fix it.
Here’s what honestly confuses me about how the AWS documentation describes permission boundaries.
On one of them, the AWS documentation describes them as a way to limit the IAM policies the user can create:
A permissions limit is an advanced feature for using a managed policy to set the maximum permissions that an identity-based policy can grant to an IAM entity.
In the following sentence, it appears that an authorization limit limits the actions that the principal can take to whom the authorization limit applies.
Limiting an entity’s permissions allows it to perform only those actions authorized by both its…