ACM.371 They may or may not be in the credentials file and deleting a file or environment variables is not enough
Part of my series on Automation of cybersecurity measures. AWS Organizations. I AM. Deploy a static website. THE Coded.
Free content on Cybersecurity Jobs | Register at Broadcast list
In the last article I talked about restricting users so that they can only change their own credentials.
While testing I was looking for how to end an active CLI session the other day because I forgot where they were, so I’m writing an article about it. I ended up digging through my file system because some of the answers I found in a quick Google search weren’t applicable.
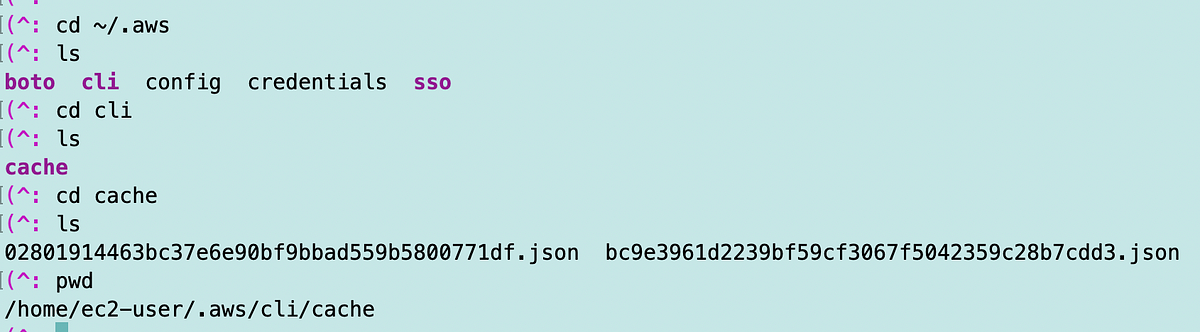
If you are using the AWS CLI and have assumed a role and want to end that session, you can delete the cached credentials. Initially I thought the cached credentials were in the credentials file. Depending on how you create the CLI profile and assume the role, this is sometimes the case.
But if you took on a role like I explained in this article, they will be in a different place.
What I wanted to do when testing the message above was clear my current MFA session so I could verify that it was still working after changing an IAM policy. You may also want to clear these files when you are finished with a particular IAM session so that no one can continue to use the session after you are finished with it.
I do all my development work on an AWS EC2 instance. I can navigate to the .aws directory as shown below and you will see a cli directory. In this directory is a cache directory. There you will find different json files depending on the number of sessions you have created.