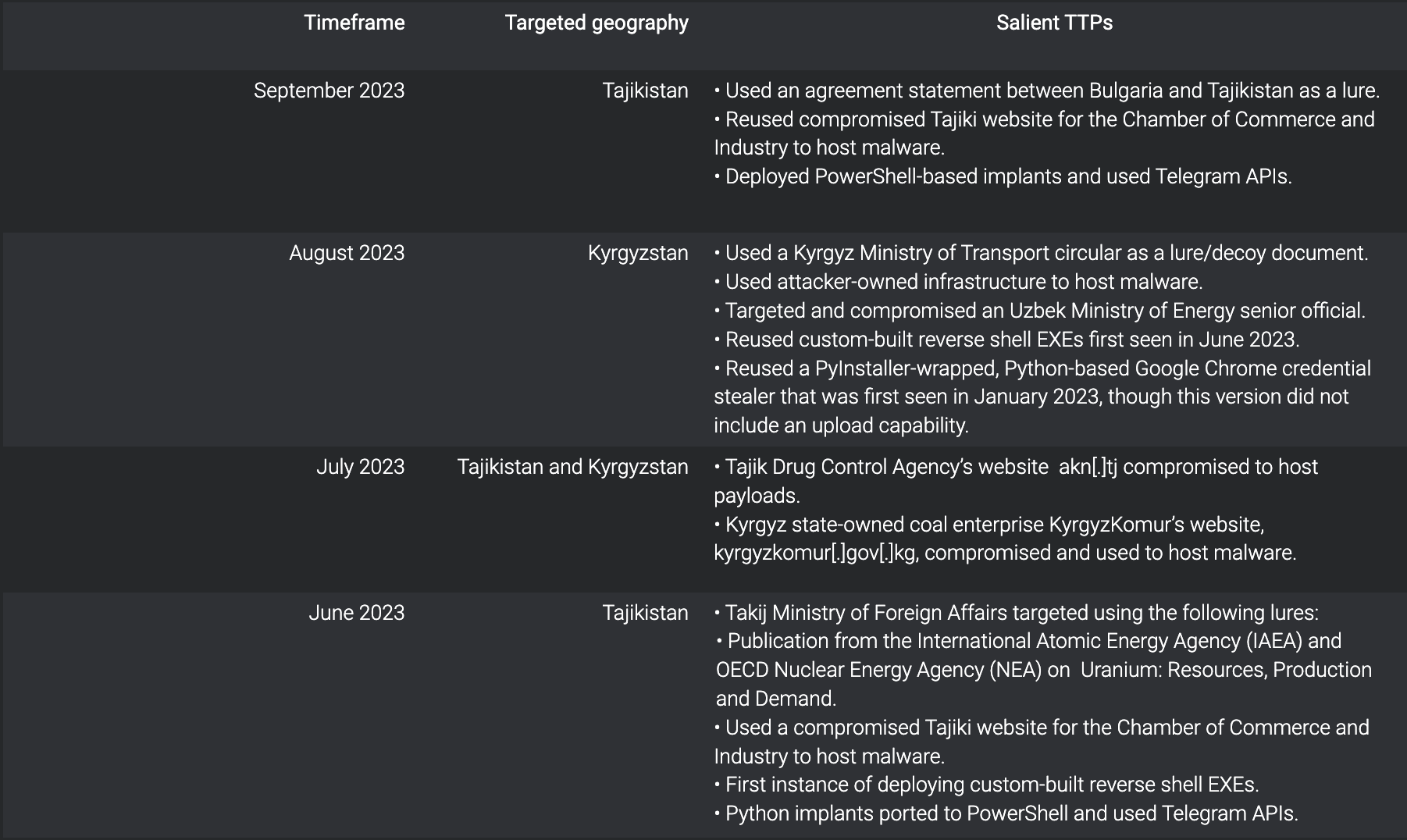
Hackers believed to be based in Kazakhstan are targeting other members of the Commonwealth of Independent States as part of a broad espionage campaign, according to new research.
Cisco’s Talos Group has spent months tracking YoroTrooper, an espionage-focused hacking group that emerged in June 2022. Researchers said the group’s targets, use of Kazakh currency and fluency in Kazakh and Russian are part of what led them to believe the hackers are based in Kazakhstan.
YoroTrooper appears to have taken defensive actions to protect the Kazakh state-owned email service and only attacked the Kazakh government’s anti-corruption agency.
Cisco Talos threat researcher Asheer Malhotra told Recorded Future News that the group actively attempted to conceal its operations to make it appear that the attacks were coming from Azerbaijan in an attempt to “generate false flags and ‘to mislead “.
“In terms of modus operandi, their tactics and tools are not very sophisticated, but YoroTrooper has still had substantial success in compromising targets in CIS (Commonwealth of Independent States) countries over the past two years, thanks to their aggressive attempts. to target their victims. Additionally, the threat actor shows no signs of slowing down despite Cisco Talos’ initial disclosure detailing YoroTrooper’s activities earlier this year,” Malhotra said.
Cisco Talos hunted attacks involving institutions and officials in Azerbaijan, Tajikistan, Kyrgyzstan and Uzbekistan, using VPN services to make it appear that their hacks originate from Azerbaijan.
Hackers compromised several public websites and accounts belonging to government officials between May 2023 and August 2023.
Most attacks start with phishing emails and deploy tailor-made malware that allows the group to steal data and credentials.
Countries attacked by YoroTrooper. Image: Cisco Talos
Researchers found that hackers were using Russian to try to debug their tools while visiting many websites written in Kazakh. In June, hackers began using Uzbek in their code, another language widely spoken in Kazakhstan.
Hackers use cryptocurrency to pay for operating infrastructure such as domains and servers, while checking “conversion rates between Kazakh tenge (KZT), the official currency of Kazakhstan, and Bitcoin (BTC) on Google “.
The group also conducts security scans for mail(.)kz, the Kazakh state-owned email service, and monitors the platform for possible security vulnerabilities. Although much of the activity passes through Azerbaijan, Cisco Talos found evidence that hackers do not speak the Azerbaijani language: they regularly visit translation sites and check Azeri-to-Azerbaijani translations. Russian.
Cisco Talos noted that since their March 2023 Report on YoroTrooper – which details the group’s attacks on a European Union health agency, the World Intellectual Property Organization and several CIS countries – they have significantly expanded their tools and tactics.
The group is using new, custom-made implants and has ditched other strains of malware it previously used.
“YoroTrooper’s targeting of government entities in these countries may indicate that the operators are motivated by Kazakh state interests or working under the direction of the Kazakh government,” the researchers said.
The group uses vulnerability scanners and open source data from search engines such as Shodan to find vulnerabilities in their target’s infrastructure. They used these tools to compromise three Tajik and Kyrgyz public websites and hosted malware payloads there this summer, with some malware still hosted as of September 2023.
The compromises included the websites of the Tajikistan Chamber of Commerce, the country’s Drug Control Agency and Kyrgyzstan’s state-owned coal company. An official from Kyrgyzstan’s Ministry of Transport and Roads was also targeted, along with other officials from Uzbekistan’s Energy Ministry.
Cisco Talos also saw the group adjust its tactics in light of their March report about hacking campaigns that allowed them to steal credentials, browser histories, system information and screenshots.
Malhotra said that while it is not common to see CIS countries hacking each other, cybersecurity researchers have seen a recent increase in cyberattacks in that region of the world.
“Given their proximity to Europe, Central Asia, Russia and China, it would seem natural for the CIS countries to develop intelligence capabilities based on actions in cyberspace to support their political, economic advances and military,” Malhotra explained.
Future saved
Intelligence cloud.
No previous articles
No new articles
Jonathan Greig
Jonathan Greig is a breaking news reporter at Recorded Future News. Jonathan has worked as a journalist around the world since 2014. Before returning to New York, he worked for media outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.


