Part of my series on Automation of cybersecurity measures. Batch job security. I AM. S3. Deploy a static website. THE Coded.
Free content on Cybersecurity Jobs | Register at Broadcast list
In the last article, I modified the generic application policy used by our Lambda functions to manage S3 read and write buckets.
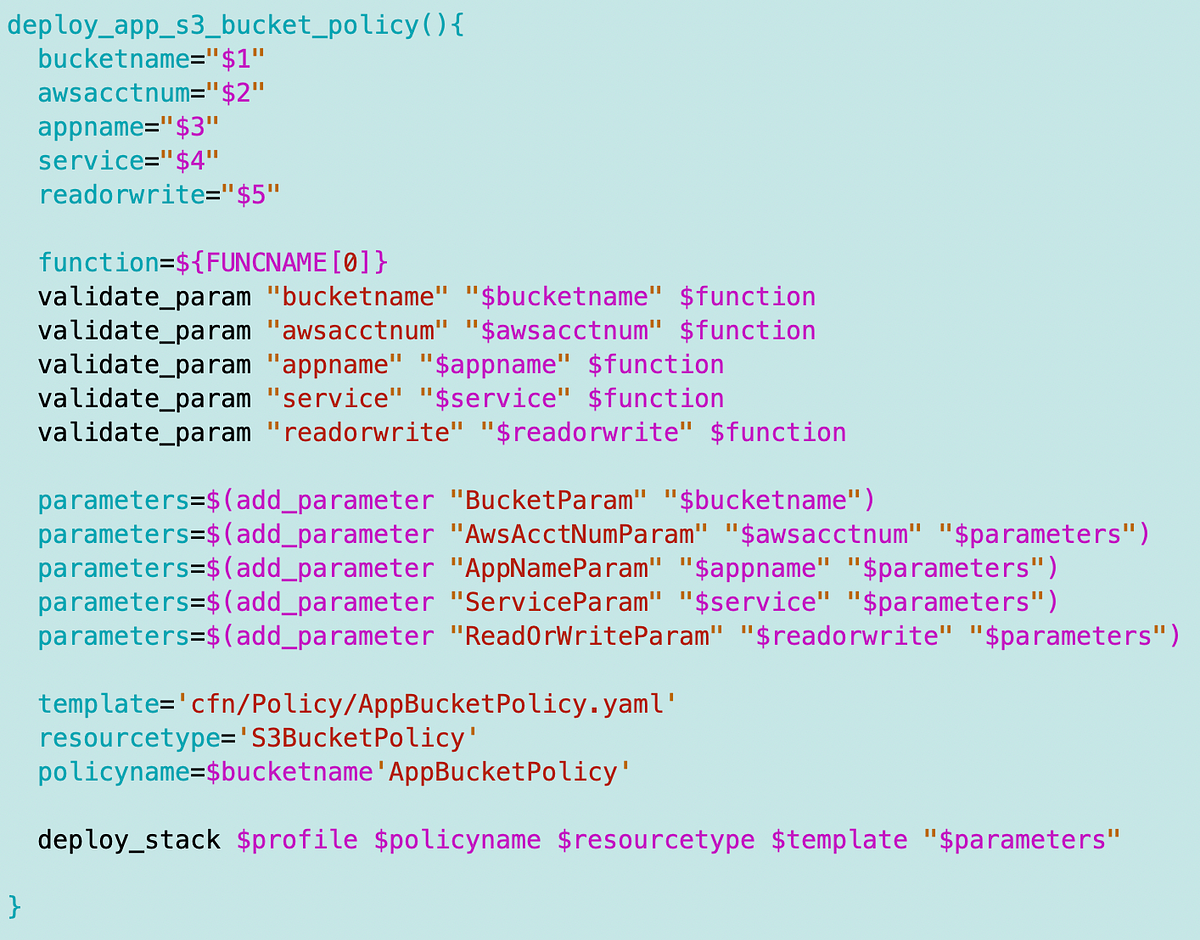
In this article, I will try to modify our existing S3 bucket template to allow applications to access S3 buckets.
Remember that I have a generic bucket template. I plan to change some things in this model later. I don’t like that it uses account numbers in bucket names, but this was a workaround for another issue for testing purposes. We don’t really need to change this bucket model. We have already used it to deploy the S3 bucket in a previous article which will host our test website.
What we need to add is an AWS Bucket policy. The CloudFormation for this looks like this:
https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/aws-resource-s3-bucketpolicy.html
Note that I’m getting an error on this page at the moment, but I’m sure AWS will fix it shortly. I am currently using page caching in Google.
Here is the example bucket policy on the page:
We’ve explored what we need to add to this policy to allow cross-account access to a user. We can do the same thing with a role ARN.