ESET Research
ESET researchers reveal increasing sophistication of threats affecting the LATAM region by employing evasion techniques and high-value targeting.
October 17, 2023
•
,
3 minutes. read

Much like the life and mysterious disappearance of Pharaoh Tutankhamun, also known as King Tutankhamun, the threat landscape in Latin America (LATAM) remains shrouded in mystery. This is mainly due to the limited global attention paid to evolving malicious campaigns in the region. Although notable events like ATM attacksTHE Banking Trojans born in Braziland the Cyber espionage with a machete operations have received media coverage, we are aware that there is more to say.
Alongside how the archaeological excavation of King Tutankhamun’s tomb shed light on ancient Egyptian life, we set out on a journey to delve into the less publicized cyber threats affecting Latin American countries. Our initiative, called Operation King TUT (The Universe of Threats), sought to explore this important threat landscape. On October 5, we presented the results of our comparative analysis to the Virus Bulletin Conference 2023: the full conference document can be read here.
In the analysis, we chose to look back at various publicly documented campaigns targeting the LATAM region between 2019 and 2023, as shown in the timeline below. All of these cybercriminal activities are detected exclusively in Latin America and are not associated with global crimeware. Since each of these operations has its own characteristics and does not appear to be linked to any known threat actor, it is highly likely that multiple actors are at play.
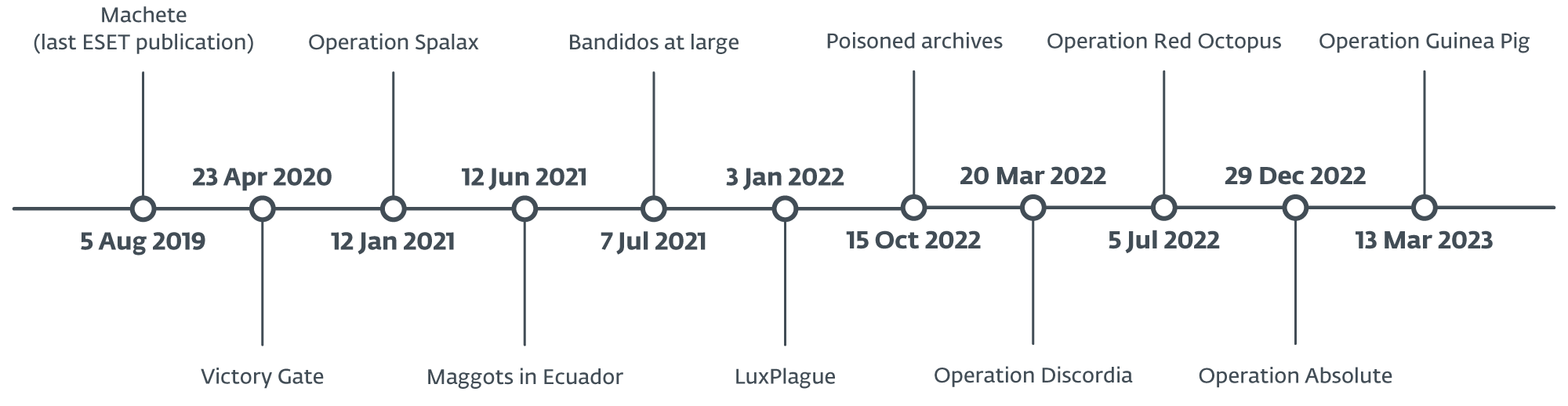
Our research revealed a notable shift from simplistic, opportunistic crimeware to more complex threats. In particular, we’ve seen a shift in targeting from a general audience focus to high-level users, including businesses and government entities. These malicious actors continually update their tools, introducing different evasion techniques to increase the success of their campaigns. Additionally, they have expanded their crimeware activity beyond Latin America, mirroring the trend seen in Banking Trojans born in Brazil.
Our comparison also shows that the majority of malicious campaigns observed in the region are directed towards enterprise users, including government sectors, primarily using spearphishing emails to reach potential victims, often posing as organizations recognized in specific countries in the region, particularly governmental or fiscal. entities.
The precision and specificity observed in these attacks indicate a high level of targeting, indicating that the threat actors have detailed knowledge of their intended victims. In these campaigns, attackers use malicious components such as downloaders and droppers, mainly created in PowerShell and VBS.
Regarding the tools used in these malicious operations in Latin America, our observations indicate a preference for RATs, notably the njRAT and AsyncRAT families. Additionally, in campaigns primarily targeting government entities, we identified the use of other malware families like Bandook and Remcos, albeit to a lesser extent.
Based on the findings resulting from our comparison, we believe that there is more than one group behind the proliferation of these types of campaigns and that these groups are actively studying different techniques and means to make their campaigns as successful as possible. Furthermore, we believe that the socio-economic disparities prevalent in Latin America may influence the modus operandi of attackers in this region, although this particular aspect is beyond the scope of our research. The full VB2023 conference document on Operation King TUT is available here.
Aggregated indicators of compromise (IoC) are available at our GitHub repository.
For any inquiries about our research published on WeLiveSecurity, please contact us at menaceintel@eset.com.
ESET Research offers intelligence reports and private APT data feeds. For any inquiries about this service, visit ESET Threat Intelligence page.


