Genetic testing giant 23andMe has confirmed that a data scraping incident allowed hackers to access sensitive user information and sell it on the dark web.
Information from nearly 7 million 23andMe users was Free for sale on a cybercriminal forum this week. The information included an origin estimate, phenotype, health information, photos, identification data and much more. 23andMe processes saliva samples submitted by customers to determine their ancestry.
When asked about the post, the company initially denied the legitimacy of the information, calling it a “misleading claim” in a statement to Recorded Future News.
The company later said it was aware that some 23andMe customer profile information had been compiled through unauthorized access to individual accounts enrolled in the DNA Relative feature – which allows users to choose whether the company shows them potential matches with loved ones.
“We have no indication at this time that there has been a data security incident within our systems. Rather, the preliminary results of this investigation suggest that the login credentials used in these access attempts may have been collected by a malicious actor from data leaked in incidents involving other online platforms where users recycled their login credentials,” they said.
“We believe that the threat actor then, in violation of our terms of service, accessed 23andme.com accounts without authorization and obtained information from these accounts. We take this matter seriously and will continue our investigation to confirm these preliminary results.
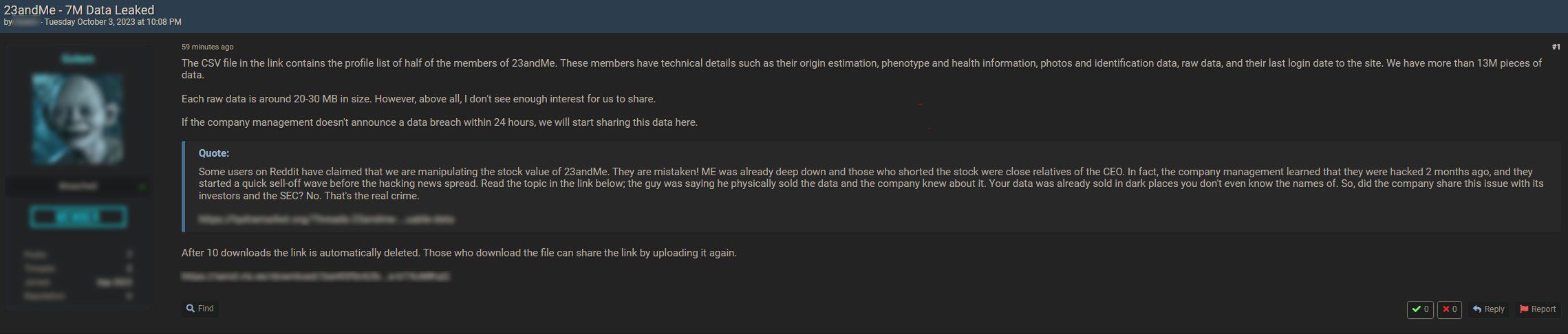
A screenshot of the 23andMe data release on the BreachForums site.
When asked how compromising a handful of user accounts would give access to millions of users, the spokesperson said the company did not believe the threat actor had access to all accounts , but instead gained unauthorized access to a much smaller number of 23andMe accounts. and extracts data from their relative DNA matches.
The spokesperson declined to confirm the precise number of customer accounts affected.
Anyone who has opted in to DNA Relatives can view the basic profile information of others who make their profiles visible to DNA Relative participants, a spokesperson said.
Genetically related users can access ancestry information, which is clearly shown to users when they create their DNA Relatives profile, the spokesperson added.
Once the company has more information about the investigation, they said, it will determine the best approach to notifying affected customers.
“A shoddy job”
The incident shows how vulnerable a company’s customer data can be even if intruders don’t penetrate deep into its network.
A researcher contacted Recorded Future News after reviewing the leaked database and found that much of it appeared real. The researcher spoke on condition of anonymity because he found the information of his wife and several family members in the leaked data set. He also found other acquaintances and verified that their information was accurate.
The researcher downloaded two files from the BreachForums publication and discovered that one of them contained information on 1 million 23andMe users of Ashkenazi heritage. The other file included data on more than 300,000 Chinese heritage users.
The data included profile and account ID numbers, names, gender, year of birth, maternal and paternal genetic markers, ancestral inheritance results, and data indicating whether each user opted in or not 23andme health data.
“It appears the information was taken from user profiles which are supposed to be shared only between DNA matches. So even though this particular leak does not contain genomic sequencing data, it is still data that should not be publicly available,” the researcher said.
“23andme seems to think it’s no big deal. They keep telling me that if I don’t want this information shared, I shouldn’t opt for the DNA Parents feature. But this minimizes the importance of this data which should only be visible to DNA relatives, and not to the public. And the fact that someone was able to scrape this data from 1.3 million users is concerning. The hacker reportedly has more data that he has not yet disclosed.
The researcher added that he discovered another issue where someone could enter a 23andme profile ID, like those included in the leaked dataset, into their URL and see someone’s profile.
The data available through this system only includes profile photos, names, birth years and location, but does not include test results.
“It is very concerning that 23andme has such a significant flaw in the design and security of their website, where they freely expose people’s information simply by typing a profile ID into the URL. Especially for a website that deals with people’s genetic data and personal information. What shoddy work on the part of the company,” the researcher said.
“I have tried contacting 23andme, but they continue to deny that there is anything wrong and respond with sweeping answers. I don’t know how to prove it without doxxing myself. But it’s pretty serious and no one takes it seriously.
The security policies of genetic testing companies like 23andMe have come under increased scrutiny from regulators in recent weeks. Three weeks ago, genetic testing company 1Health.io agreed to pay the Federal Trade Commission (FTC) a fine of $75,000 to resolve allegations that it failed to secure sensitive genetic and health data, retroactively revised its privacy policy without notifying or obtaining consent from customers whose data it had obtained, and misled customers about their ability to delete their data.
Future saved
Intelligence cloud.
No previous articles
No new articles
Jonathan Greig
Jonathan Greig is a breaking news reporter at Recorded Future News. Jonathan has worked as a journalist around the world since 2014. Before returning to New York, he worked for media outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.