The US government and the White House like to talk tough on ransomware. If you listen to Joe Biden, the fight against Ransomware is a top priority for the US government. He spent time convincing the G7, NATO and the EU to pledge how serious they are about fighting Ransomware, a Connecticut judge has ruled that spammers who distribute Ransomware should go free.
From 2007 to 2012, I led a project called UAB Spam Data Mine. The main spammer in the early years was Peter Levashov, who first led Storm Worm and then the Waledac botnet. We regularly blog about its spam campaigns. Here are some examples :
15OCT2007 – “Is your fifth grader smarter than a laughing cat?“
17NOV2007 – “Private detective spam“
December 26, 2007 – “A stormy Christmas and a new botnet year”
16JAN2008 – “The storm loves you!“
JUNE 06, 2008 – “A romantic June storm“
01JUL2008 – “July Storm Worm gives us some love”
JULY 03, 2008 – “Storm Worm greets our nation on the 4th!“
JULY 22, 2008 – “Amero to replace the dollar? Could Storm Worm be right?“
JULY 29, 2008 – “FBI and Facebook: Storm Worm is all wrong!“
03JAN2009 – “Good year! Here is a virus! (New Year Postcard Malware)“
25FEB2009 – “Are you short of money? Beware of CyberCriminals Coupon Offers”
MARCH 16, 2009 – “Waledac: a fake dirty bomb in your town“
MARCH 18, 2009 – “Carders fight against spam – carder.su”
09APR2009 – “Is there a Conficker E? Waledac makes a gesture…“
15APR2009 – “Waledac switches to SMS spy program”
29APR2009 – “Waledac Let’s move on to . . . Canadian pharmacy?“
MARCH 03, 2010 – “Spam Botnets – Welcome Strategies”
JULY 03, 2009 – “Are you ready for Independence Day fireworks? Waledac is!“
December 31, 2009 – “Waledac New Year Card”
In 2008, Levashov was secretly indicted on spam charges and federal agents were deployed to Moscow to seek out Levashov. I actually created a Google Map showing that every city in Russia had thousands of infected IP addresses that were being used to send spam. Despite a mountain of evidence, he was protected. He continued to spam, but honestly I gave up on the idea of him being captured.
After others attempted to take down the Kelihos botnet, it re-emerged as a spam campaign leveraging the Boston Marathon bombing. I tried again to get law enforcement interested in him at that time. A criminal who would take advantage of the Boston Marathon attack to relaunch the new version of his botnet would surely deserve to be interested. Nothing. I remembered 2009 and was told, “The Russians are protecting him.”
10APR2013 – “New spam attacks represent 62% of our spam!“
17APR2013 – “Boston Marathon Explosion Spam Leads to Malware”
18APR2013 – “Boston Explosion Spammer Turns to Texas Fertilizer Plant Explosion”
TrendMicro confirmed that it was also Kelihos in its post:
16APR2013 – “The Kelihos Worm Emerges and Takes Advantage of the Boston Marathon Explosion”
In 2016, we decided to try again, with the “Kelihos Must Die” task force. We provided regular updates on the bad things Kelihos was doing. Students in my lab, led by my friend (now) Dr. Arsh Arora, were producing daily documentation of the botnet’s behavior, and we were starting to get excited that something might actually happen this time . We believed Kelihos was sending FOUR BILLION SPAM A DAY and took the time to prove that it was launching ransomware attacks, banking Trojan attacks, and phishing attacks. Levashov would spam to deliver whatever payload you paid him for.
JULY 09, 2016 – “Kelihos botnet distributes Dutch WildFire ransomware“
04AUGUST2016 – “American Airlines spam from Kelihos delivers ransomware“
AUGUST 12, 2016 – “Kelihos botnet sends Panda Zeus to German and UK banking customers“
AUGUST 16, 2016 – “Kelihos botnet sends geotargeted phishing from Desjardins to Canadians“
AUGUST 30, 2016 – “Amazon gift card from Kelihos!“
September 14, 2016 – “Kelihos Long Lasting Pill Spam“
09NOV2016 – “Kronos banking Trojan and Kelihos geotargeting“
30NOV2016 – “NoMoreRansom aka Troldesh Ransomware delivered by Kelihos“
01FEB2017 – “Kelihos infection spreads through Thumb Drive and continues geotargeting”
And then on April 20, 2017, it was over!
Spanish authorities arrested Levashov in Barcelona and he was sent to the United States to stand trial.
After initially pleading not guilty, he changed his plea to guilty on September 12, 2018. He admitted to controlling and operating Storm, Waledac and Kelihos, and to spreading spam spreading other malware, including banking Trojans and ransomware. He admitted to actively promoting the Kelihos botnet and its ability to distribute spam and malware, and that he did so in order to enrich himself. He admitted to stealing identities and credit cards, then buying and selling them.
The U.S. Attorney handling the case filed this sentencing memo telling the judge what the Justice Department thought should be done in this case:
And just to make things clear, they used the sentencing guidelines and included this helpful sentencing recommendation (required by law) in the sentencing memo to help the judge understand what the law says should be done:
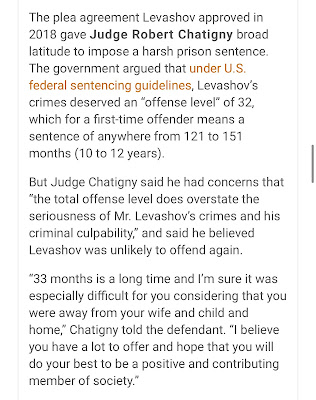
The judge instead decided that he would ignore the Justice Department’s recommendation and did so based solely on his own intuition (as reported by Brian Krebs 🙂
“the total level of the offense overstates the seriousness of Mr. Levashov’s criminal culpability” and said he believed Levashov was unlikely to reoffend. “I believe you have much to offer and I hope you will do your best to be a positive and contributing member of society.” — Judge Robert Chatigny of Connecticut
And with that, a single judge in Connecticut decided that this CAREER CRIMINAL was “unlikely to re-offend” and felt the charges were overstated AND LET HIM GO.
So much for the government’s priority to stop ransomware.
The message that this incompetent judge has just delivered to the criminal community is the following:
“Spam all you want, as long as you have a good lawyer and an incompetent judge, spam clearly doesn’t matter in the United States.”