Part of my series on Automation of cybersecurity measures. Application security. Penetration testing. Data breaches. Deploy a static website. THE Coded.
Free content on Cybersecurity Jobs | Register at Broadcast list
Often people talk about a Man in the Middle (MITM) or sometimes called a Monkey-in-the-middle attack and said to be necessary for a particular attack to work. But what does that really mean?
There are different times when these attacks can occur. In order to properly assess risk and defend against MITM attacks, you need to understand where they can occur and the implications of different types of MITM attacks. In some cases, the risks associated with the malware that enabled the MITM attack itself are greater than the vulnerability it facilitates.
In other cases, malware is not necessary for a MITM attack. Traffic can be inspected simply because it is unencrypted and passes through a particular network device. There are different ways to approach these different points of attack.
Although MITM is related to encrypted traffic, HTTPS, HSTS, and other types of attacks, understanding the point of attack and how it works will help you understand if a particular security control is relevant to that particular attack. This will also help you understand the level of risk and where to focus your efforts to deal with a particular type of attack.
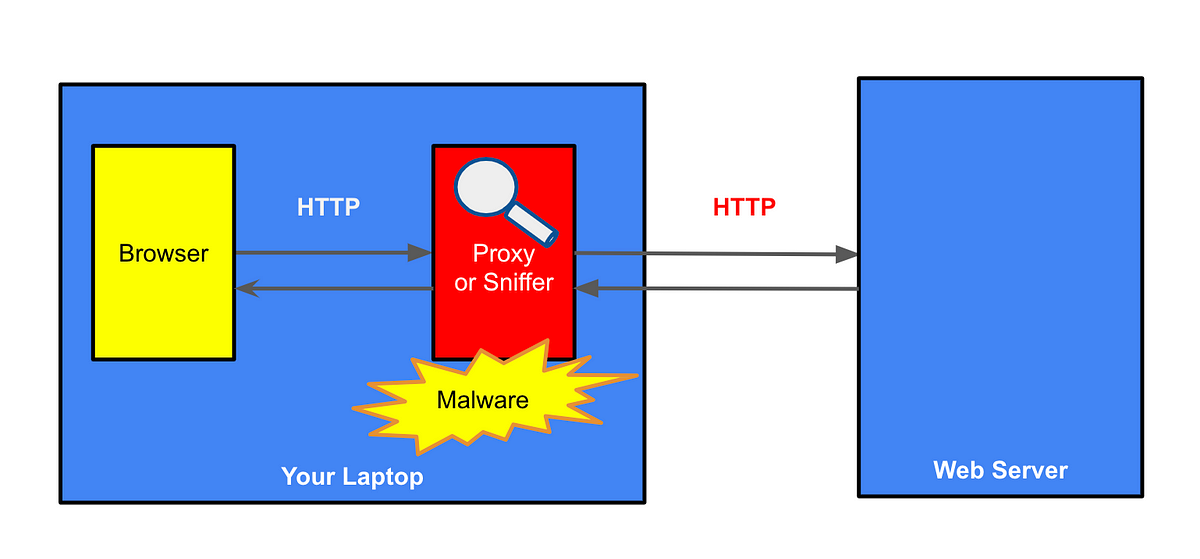
MITM on your laptop
Malware can get onto your laptop or personal computer. In this scenario, an attacker can read any unencrypted traffic you send over the network using a sniffer.
Not only can they read traffic, but they can also modify the traffic sent back to your browser. Maybe they will return malware to your browser. This doesn’t make much sense if they already have malware on your system, but think about how this might be useful when the malware is positioned in the other locations described later in the article.