ACM.404 After applying an SCP that requires multi-factor authentication for all non-role actions, how does cross-account AWS Organizations role work?
Part of my series on Automation of cybersecurity measures. AWS Organizations. I AM. Deploy a static website. THE Coded.
Free content on Cybersecurity Jobs | Register at Broadcast list
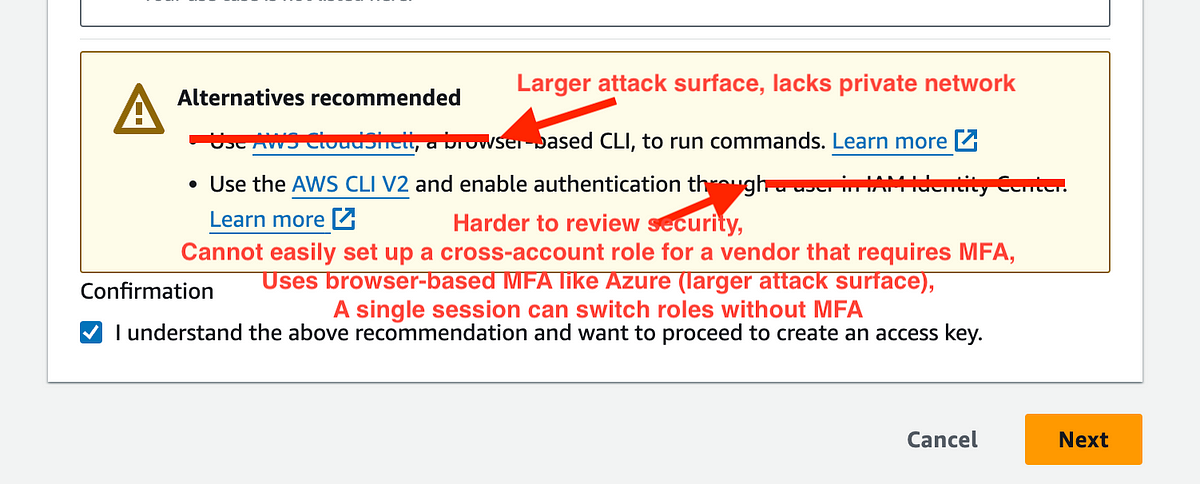
In the last article I added a Service Control Policy (SCP) that enforces multi-factor authentication for all actions except those taken by roles (hopefully). I still have to test it.
In this article, I want to test access to the AWS Organizations role deployed with my orgadmin account. I explain what this account is and how I use it here:
The AWS Organizations role is automatically deployed when you add a new account to an AWS Organization. You can set the role name, which I did in my CloudFormation template. Then I define the role name in the stack outputs so that it’s easy to see the AWS Organizations role for any account.
Here’s what I don’t know for sure based on the AWS documentation. It states (as of this writing) that the management account is not affected by AWS SCPs.
The role we are going to take on is not in the management account. It’s in a child account. But the user who will assume the role is in the management account.
- So, does the MFA policy apply because the action of assuming the role occurs in the child account?
- Or does the MFA policy not apply because the user performing the action is in the management account?